禁用软件现象的普遍性
近年来,随着科技的发展和数字生活的深入,各种类型的软件在我们的日常生活中扮演着越来越重要的角色。然而,一些软件由于其不当使用或潜在风险而被视为“禁用软件”。这些程序通常会对设备安全、用户隐私以及网络环境造成威胁,因此引发了广泛关注。
用户需求与软硬件兼容性
很多时候,用户希望能够顺利运行各种应用,而不受任何限制。系统要求极高或者与某些主流设备不兼容的软件可能导致用户面临困扰。在寻找替代方案时,了解哪些应用可以满足相关功能同时又不会带来安全隐患成为一种迫切需求。此外,对于企业来说,更是需要确保所选工具能有效提升工作效率,同时避免因使用未授权或危险软件而遭遇法律风险。
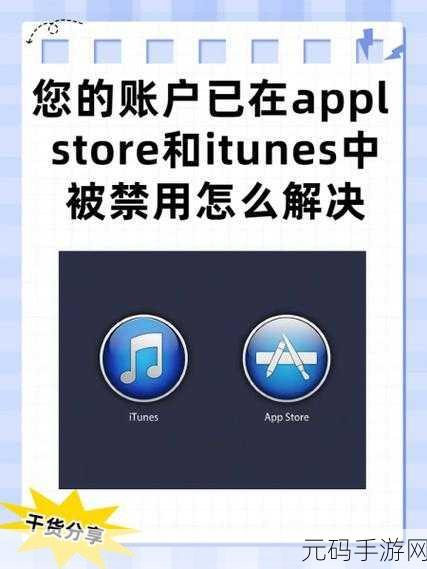
数据保护意识增强
人们对个人信息泄露问题愈加敏感,这推动了对于可信赖软件下载源的重要性的认识。许多知名平台开始积极标注下载内容的来源,以便帮助消费者识别那些值得信任的软件。同时,也有不少第三方评测网站提供详细分析,对比不同版本之间是否存在恶意代码。这一系列措施不仅提高了大众的数据保护意识,也促进了整个行业朝向更加透明和负责任的发展方向。
技术更新催生新解决方案
为了应对禁用软件的问题,开发者们不断推出新的解决方案。例如,提高防火墙和杀毒软件的性能,使得即使面对未知病毒也能及时阻止侵害。此外,一些创新型公司尝试通过人工智能技术检测并实时拦截有潜在危险的软件,从根本上减少这类程序进入普通消费市场。而虚拟化技术则为一些特定领域提供了一种隔离环境,让敏感操作可以脱离真实网络进行,从而降低风控需承受压力。
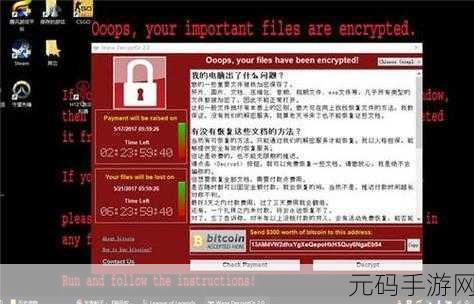
社区监督的重要性
User feedback and community reviews play a crucial role in identifying potentially harmful software. Online forums, social media platforms, and dedicated app review sites offer users an opportunity to share their experiences with various applications. This peer-to-peer exchange of information helps create a culture of accountability among developers while empowering consumers to make informed decisions when selecting apps.
aVPN及其作用发挥空间
The use of VPNs has become increasingly popular as individuals seek ways to protect their online activities from prying eyes. While some may not realize it yet, certain disallowed software can also be effectively managed through the use of reliable VPN services that encrypt user data traffic. By utilizing these tools responsibly, one can minimize exposure to risks associated with accessing restricted content or using vulnerable applications.
A/B测试中的伦理考量
- Your privacy is paramount — choose trustworthy sources for downloads!
- Breach incidents continue highlighting vulnerabilities present within widely used programs worldwide.
- The rise in cybercrime necessitates constant vigilance against emerging threats resulting from unchecked access points across networks globally!



